->>Go Green
->>Heal the world! Make it a better place!
->>Earth needs YOU.
->>Let's face it! It's easier saving paper than planting trees.
->>Save our planet think green.
->>Save Paper, Save Trees, Save the Planet!
->>Take care of earth and she will take care of you
Are you trying to conduct a survey or research using a questionnaire and are worried of the burden that comes with such an exercise; designing the form in the traditional MS word, printing the form, distributing the form, collecting the completed and printed forms, issuing countless reminders for feedback, and finally, compiling and manually entering the responses into a spreadsheet for analysis. Not forgetting the direct costs that come with these tasks; printing fees, transport fees, Telephone fees (yes! Remind the respondents), data entry fees (yes! Bulk surveys). This method also reduces data entry errors and most importantly, don't forget that we are trying to "Go Green" so please embrace the "Green Revolution".
Well, in this article we will change all that hustle into “Click, Click and Send”. Fun, isn’t it?
We will create an electronic copy of the questionnaire(or eform) which you will then send out to your target respondents, each respondent will directly fill the questionnaire and then email the information back to you by just clicking a button right in the e-form. We will then import all the returned data files into excel in a single move and your data will be ready for analysis.
A survey/research that was probably going to take you months to finish will be done in just a few days depending on how fast your respondents are at returning email.
Tools: Use Adobe LiveCycle Designer ES in standalone mode (part of the Adobe Design Premium CS4).
Step 1:
Create the eform using Adobe LiveCycle Designer. This is the form that you distribute to the people who will fill the form, “Adobe LiveCycle Designer Help” has a very nice “Quick Start Tutorials” with a very well explained and elaborate example; “Creating an office function survey form”. It would really be a waste of time for me to go back through the same steps, so please use this help guide to learn how to design your first eform. It’s very simple. And if you need an overview before you acquire Adobe LiveCycle; http://help.adobe.com/en_US/livecycle/8.2/overview.pdf
Step 2:
Save the questionnaire as a PDF document to your local PC. Make sure your eform has the “[Submit by Email]” button.
Step 3:
Connect to your internet email account (e.g. gmail or yahoomail) or launch your local email application (e.g MS Outlook) and attach the questionnaire.
Step 4:
Send out your eform to the target respondents, include some brief instructions on how they should fill the eform and send it back to you. When a respondent clicks the “[Submit by Email]” button in the eform, it generates a report/data file in XML format. If the respondent is using a local email application on their machine, it will automatically launch it and attach the report file plus the email address of the sender (your email address). If the respondent is using an internet email account e.g. gmail or yahoomail, it will prompt him/her to save the file to his/her local PC which they can later send as an attachment (equally simple). The best way is to first try the whole process by yourself before you send it out so that you can get the real feel of what your respondents will be going through. Try both for a respondent who is using a local email application or an internet email. Then you can write brief and precise instructions to your respondents. End users only require Adobe Reader to electronically fill the eform and send the eform data to the originator of the eform.
Step 5:
You will receive the report as an XML document, download it to your local PC and rename it report1, repeat this for all the responses received by renaming them; report2, report3, report4 … report(x).
Step 6:
Open the orignal eform/questionnaire that you created and saved on your local PC, this will open in Adobe Acrobat Pro. Go to “Forms” > “Manage Form Data” > “Merge Data Files into Spreadsheet”
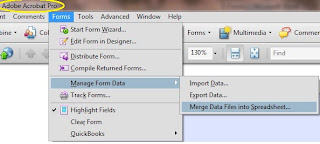
Step 7:
Click “[Add Files]” to add all the report files and click “[Export]”; this will create one spreadsheet containing all the data from all the report files.
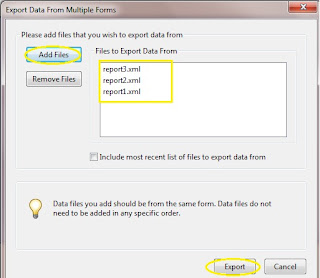
Save the generated spreadsheet and you are now ready to analyze your data. Have a fun and good luck.













